TCP/IP
TCP connection
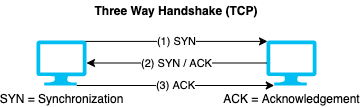
Three-way handshake
- Also known as • 3-way handshake • three-way handshake • 3 way handshake • three way handshake
- Establishes a TCP connection
- 📝 Sender:
SYN→ Receiver:SYN ACK→ Sender:ACK ACKis then set in every packet sent after the handshake
Termination
- 📝 Sender:
FIN→ Receiver:ACK FIN→ Sender:ACK
IPv4
- IPv4 loopback address (localhost of your own machine) is
127.0.0.1
IPv4 address types
- Unicast
- Acted on by a single recipient
- Multicast
- Acted on only by members of a specific group
- Broadcast
- Acted on by everyone in the network
- Two types:
- Limited broadcast
- Delivered to every system inside a domain using:
- IP: 255.255.255.255
- MAC: FF:FF:FF:FF:FF:FF
- Ignored by routers
- Delivered to every system inside a domain using:
- Directed broadcasts
- Sent to all devices on subnet
- Use subnets broadcast address
- E.g. if subnet is 192.168.17.0/24 then it uses 192.168.17.255
- Routers may take action on the packets.
- Limited broadcast
IPv6
- IPv6 uses a 128-bit address instead of the 32-bit IPv4 version
- Represented as eight groups of four hexadecimal digits separated by colons
- E.g.
2001:0db8:85a3:0000:0000:8a2e:0370:7334
- E.g.
- Leading zeros can be removed e.g.
- Original:
2001:0001:0002:0003:0004:0005:0006:0007 - Short:
2001:1:2:3:4:5:6:7
- Original:
- The loopback address is
::1- Shortened version of
0000:0000:0000:0000:0000:0000:0000:0001
- Shortened version of
CIDR
Method of the representing IP addresses
📝 Easy way to find out CIDR ranges, remember:
/24 255.255.255.0 256- So
/24gives 256 IP addresses,/25gives 128,/26gives 64 and so on.
- So
IPv4 Notation
CIDR Range Total IP Addresses Subnet mask /320 255.255/304 .225.252/2816 .255.240/2664 .255.192/24256 .255.0/221024 .248.0/204096 .240.0
TCP flags
- Used to indicate a particular connection state or provide additional information
- Size of each flag is 1 bit being either
0or1 - 📝 Flag types
- Synchronization (
SYN)- Also known as synchronization flag.
- Synchronize sequence numbers
- First step of connection establishment (3-way handshake)
- ❗ Only the first packet sent from each end should have this flag set
- Acknowledgement (
ACK)- Confirms successful packet retrieval
- Push (
PSH)- Tells receiver to process packets instead of buffering them
- Urgent (
URG)- Process packets directly before others, even if they're not complete
- Finish (
FIN):1indicate connection termination requests- Used in the last packet sent from the sender.
- Reset (
RST)1aborts the connection in response- Sent from the receiver to the sender when a packet is sent to a particular host that was not expecting it.
- Also used as
- DDoS attack, see
RSTattack - Scanning technique, see RFC 793 scans
- DDoS attack, see
- Synchronization (
Finish (FIN) vs Reset (RST)
FIN | RST |
|---|---|
| Gracefully termination | Sudden termination |
| Only one side of conversation is stopped | Whole conversation is stopped |
| No data loss | Data is discarded |
Receiver of FIN can choose to continue communicating | Receiver has to stop communication |
Push (PSH) vs Urgent (URG)
PSH | URG |
|---|---|
| All data in buffer are pushed | Only urgent data is pushed immediately |
| Data is delivered in sequence | Data is delivered out of sequence |
TCP/IP sessions
- TCP uses stateful sessions
- Connection establishment must be done before data transfer
- Session initiation
- Source sends SYN packet
- Destination responds with SYN/ACK packet
- Source sends ACK packet
- Connection stays open until closed with
FINorRSTpackets.
- Session termination
OSI model
- Conceptual model that characterizes and standardizes the communication functions
- 📝 Uses seven abstraction layers:
- Physical (bits)
- Media, signal & binary transmission
- E.g. • Cables (fiber) • Fiber • Wireless • Hubs • Repeaters
- Data link (frames)
- Physical addressing: MAC & LLC
- E.g. • Ethernet • PPP • Switch • Bridge
- Network (packets)
- Transport (segments)
- End-to-end connections and reliability
- E.g. • TCP • UDP
- Session (data)
- Sync & send to ports, inter-host communication
- E.g. • API's • Sockets • WinSock
- Presentation (data)
- Application (data)
- Physical (bits)
- See also • Firewall types per OSI Layer | Firewall • Vulnerability stack | Hacking web applications • Encryption types per OSI layer | Encryption algorithms
TCP/IP model
- TCP/IP model defines four levels:
- ❗ OSI model does not match well TCP/IP
- RFC 3439 considers layering "harmful"
- ❗ E.g. SSL/TLS does not fit in any of OSI or TCP/IP layers
- In OSI it's in layer 6 or 7, and, at the same time, in layer 4 or below.
- In TCP/IP it's in between the transport and the application layers.
TCP/IP vs OSI model
| TCP/IP | Protocols and services | OSI model |
|---|---|---|
| Application | • HTTP • FTP • Telnet • NTP • DHCP • PING | • Application • Presentation • Session |
| Transport | • TCP • UDP | Transport |
| Network | • IP • ARP • ICMP • IGMP | Network |
| Network interface | • Ethernet • PPTP | • Data Link • Physical |