Scanning networks overview
- Process of obtaining additional information about hosts, ports and services in network
- More detailed reconnaissance
- Purpose is to identify vulnerabilities in communication channels and then create an attack plan.
- Different techniques are used to identify hosts, ports, and services in the target network.
- Used by administrators to verify security policies, monitoring uptime etc.
- Can craft custom packets using different tools
Scanning types
- Port scanning: to list open ports and services
- Network scanning: to list IP addresses
- Vulnerability scanning: to discover the presence of known vulnerabilities
Scanning in IPv6 Networks
- IP supports more addresses
- Bigger search space
- More difficult and complex than IPv4
- Harder to do ping sweeps
- Supports large number of hosts in a subnet.
- Probing takes longer time
- 💡 Attacker should find addresses from logs, e-mails, traffics etc. to identify addresses.
Common ports to scan
📝 List of TCP and UDP port numbers
Port Protocol Service 21 TCP FTP (File Transfer Protocol) 22 TCP SSH (Secure Shell) 23 TCP Telnet 25 TCP SMTP (Simple Mail Transfer Protocol) 53 TCP/UDP DNS (Domain Name Server) 80 TCP HTTP (Hypertext Transfer Protocol) ❗ HTTP/3 will run over UDP 123 TCP NTP (Network Time Protocol) 443 TCP/UDP HTTPS 500 TCP/UDP IKE/IPSec (Internet Key Exchange / IPSec) 631 TCP/UDP IPP (Internet Printing Protocol) 3389 TCP/UDP RDP (Remote Desktop Protocol) 9100 TCP/UDP AppSocket/JetDirect (HP JetDirect, Printer PDL Data Stream) Read more on IANA ports list
See also • Port monitoring | Malware analysis • Common ports and services to enumerate | Enumeration
Drawing and mapping out network topologies
- Useful for identifying and understanding the topology of the target network.
- The diagram can tell the attacker how firewalls, IDSes, routers, and other devices are arranged in the network
- Information can be used for vulnerability discovery and exploit.
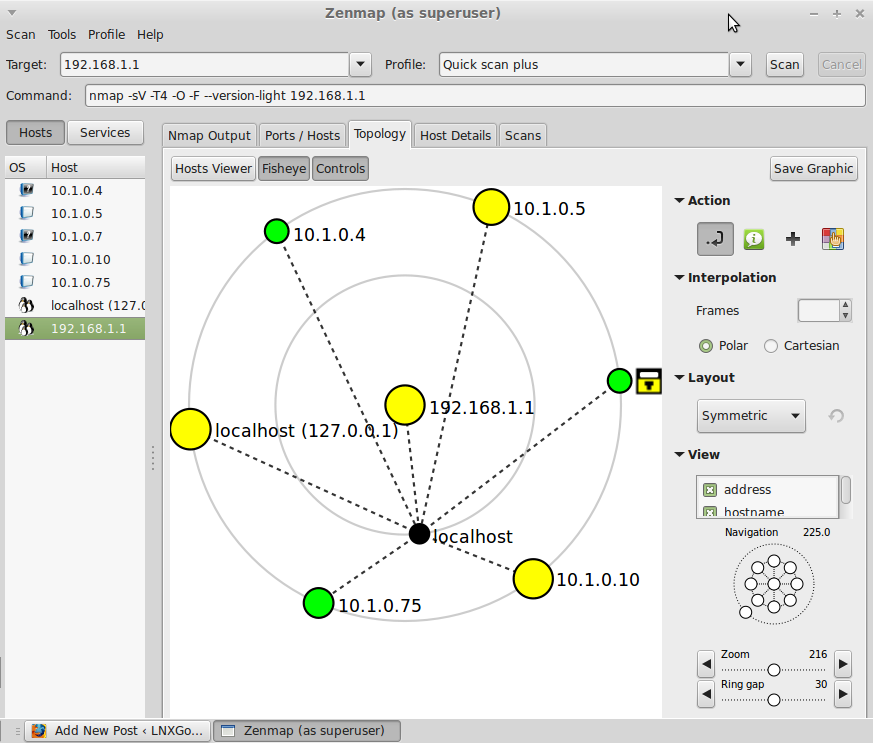
- A popular tool is
zenmap: A GUI fornmap - E.g. scanning network in a coffee shop. Run
ipconfig(windows) to get private IP address and subnet range. Then you can scan and create a map.